Using SSH Key-pairs to better secure connections to remote servers - Windows
Posted on April 11, 2014 • 4 minutes • 793 words
Table of contents
This article shows how to set up a SSH key pair to allow you to log into servers in a quick, simple and secure way from your Windows Laptop or PC. It’s certainly worth doing if you log onto remote servers regularly.
What is an SSH key-pair?
I get asked this question a lot at work, and the concept is a little bit strange if you’re new to it. A key-pair is a pair of keys which are generated at the same time by a cryptographic algorithm. They only work with each other and each key-pair is unique. A Public Key is useless without the Private Key, and this goes on your remote host, and is perfectly secure to do so.
Keys and Locks
You could think of the Public Key as a physical padlock on a door, where everyone is able to see the lock, but nobody can unlock it. Your unique private key - that you keep safe in your pocket - is the only key able to unlock the padlock. The lock is useless to anyone without the correct key.
Once your key is used with the lock, the lock becomes open and you’re able to gain access.
The process
What happens is when your client sends a connection request to the server that contains the Public Key, the server responds with an encrypted challenge request using the shared Public Key information. Your client decrypts the challenge message and responds back to the server. The secure connection is then established if the response matches the Public Key.
Key-pairs are more secure than passwords as they’re much much harder to attack via brute force. The Private Key is never transmitted to the remote host, so it can never be compromised. They’re also more convenient, as Public Keys can be saved upon your remote hosts for reuse, removing the need to manually authenticate.
Generating and using a Public/Private Key Pair on your PC

Prerequisites
Download and install Putty.
- Putty
- PuttyGen (Included with a standard Putty installation)
Tip 🚀
PuttyGen is located in C:\Program Files (x86)\PuTTY\puttygen.exe by default. Usually a shortcut to PuttyGen will not have been created on installation.
Generating a Public/Private Key Pair
-
Run PuttyGen (location shown above)
-
Click Generate and follow the on screen instruction to move the mouse around in the blank box. What this is doing is building a new strong unique key-pair based on the movements of your mouse. Your key will now appear in the Key field. Don’t close the window.
-
Copy the script below and paste into notepad
1PUBLIC_KEY="ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEAxwKhgtc86xumFtEBCyQa7kRo718BFeRMwSSRuoGMTXq8D8yMbgx7NcJJCS04gdLTbFAVhj1KX+zCIli9LOVnR5q0BgjOYfTC4lk97tA2puxJ7MMw3yf6MbuP4QIB4qKLf/GfU08Gj2oukZgN/PP8DTYxVIozYi08tae2D+qlT2+3GiwKY23VkAZ3LebKc+hvbubN7BD6BK1qGS+ctBZTdtqOAi8ZyM65GmoWqxiUqi7ZvkvcOsINFARpL406ZZbRzZONitINVU7qTfi2BxIIV14TM9FgoSUathAxa6XGrOz2wOjvjZcfI9n63HXBU/fEnovEn4Z1WZX/KDtRyTEEaQ== rsa-key-20140411"
2if [[ ! -d "$HOME/.ssh" ]]; then mkdir "$HOME/.ssh"; fi && \
3echo "$PUBLIC_KEY" >> "$HOME/.ssh/authorized_keys" && \
4chmod 600 "$HOME/.ssh/authorized_keys" && \
5chmod 700 "$HOME/.ssh/"
What does the script do?
Line 1: First of all it sets a variable containing your Public Key
Line 2: A check is performed to see if there’s an .ssh directory and creates it if there isn’t one already
Line 3: The Public Key is placed into the remote hosts’ authorized_keys file
Line 4 & 5: Finally, secure permissions are applied to the files and directories
-
Be sure to replace the contents of the
PUBLIC_KEYvariable with the contents of your Public Key -
Copy your script to your clipboard
-
Log on to a server with your password, and paste your script into the terminal
-
Going back to your PuttyGen window, now save your Private Key. Name and save your Private Key carefully. You should not share this key with anyone else, or they will be able to act as you and log onto your remote hosts!
Using Public and Private Keys with Putty
If you want to automate logging into servers, you can use your new keys to allow instant access - without having to type in your username and password every time. In regards to security, this can have benefits and drawbacks. The main drawback is that anyone with access to your laptop will be able to log into servers as you. This means locking your machine when you are away from it becomes even more important. It does however mean that obtaining your server password is very difficult for malware or other methods.
-
Open up your standard Putty window
-
Navigate to Connection > SSH > Auth
-
On this tab, enter the location of your Private Key under Private Key file for authentication:

-
Navigate to Connection > Data
-
On this tab, enter your Linux username under Login Details
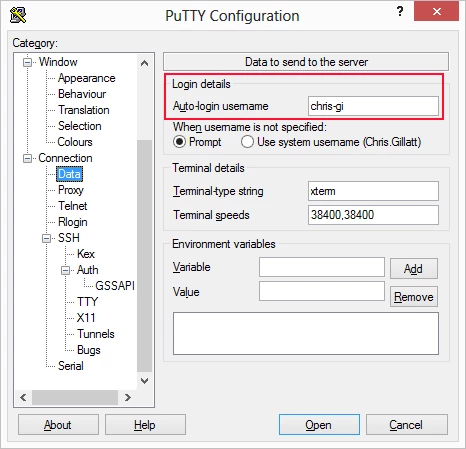
-
Navigate back to Session, type in a name for your new settings under Saved Sessions, and click Save

Once this has been completed, you should be able to simply type in an IP or hostname and click Open to automatically log you in! without entering a username or password!